Classic passwd
I forgot my password, can you give me access to the program?
Analyze flags, function calls etc using: radare2 -A -d Challenge.Challenge
Now let's check what we can find inside the main function: pdf @main
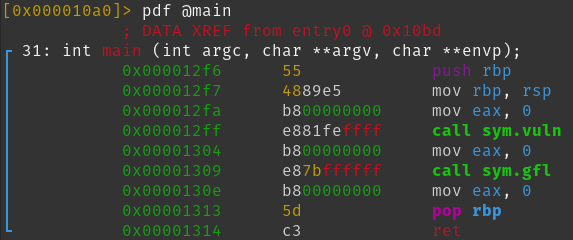
We can see a call to sym.vuln and to sym.gfl.
In order to see what lies in sym.vuln we use pdf @sym.vuln.
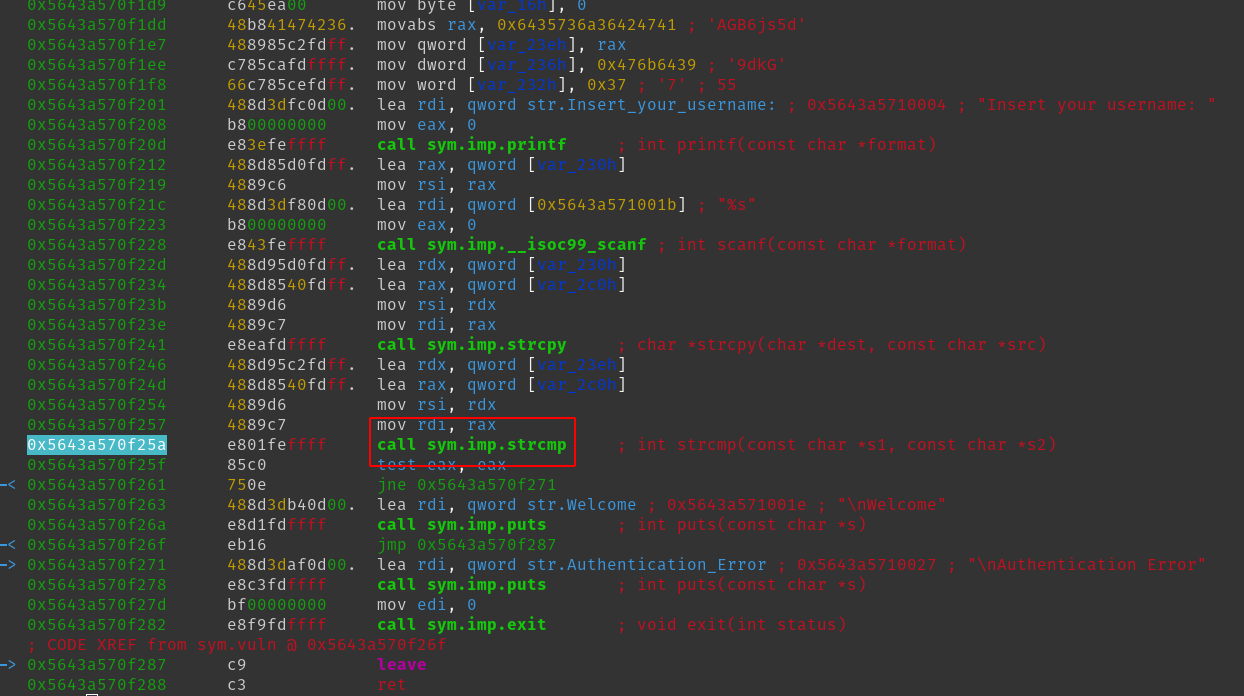
Let's set a breapoint at that call db 0x5643a570f25a and then run the application with dc.
Next let's insert a random username and then use pdf to see where we currently are in the code.
sym.imp.strcmp seems to check rsi and rdi so let's take a look at these two registers with px @<NAME>:
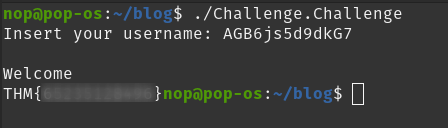
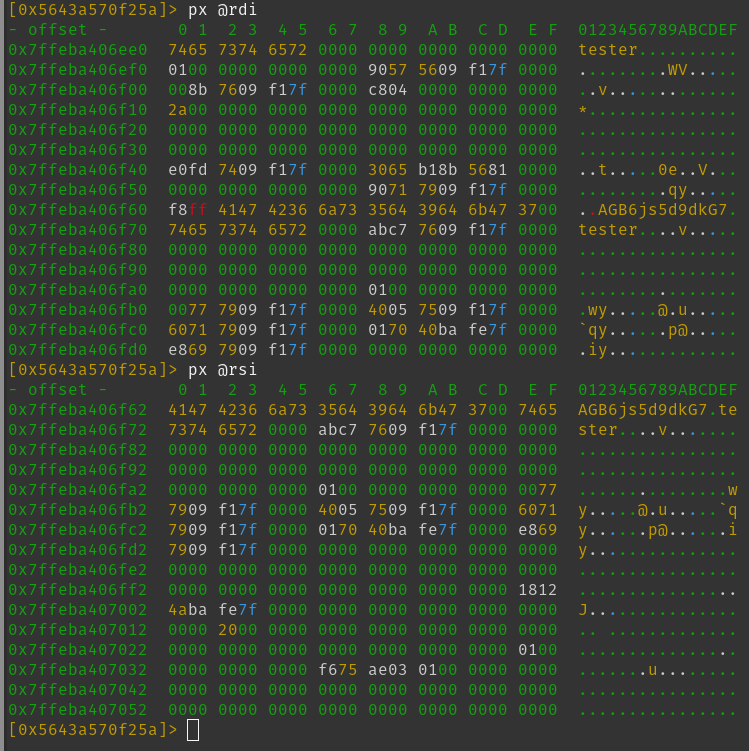 In the rdi register we can see tester (the username I entered while debugging) and in the rsi register AGB6js5d9dkG7.
In the rdi register we can see tester (the username I entered while debugging) and in the rsi register AGB6js5d9dkG7.
When using this string as an username we can now login and retrieve the flag:
Tags:
radare2, tryhackme, reversing, crackme, reverse engineering