My_dog
My Dog5 by n0ve3mber
Date: 14.03.2021
Analyze flags, function calls etc using: radare2 -A -d "My Dog5.exe"
Now let's check what we can find inside the main function: pdf @main
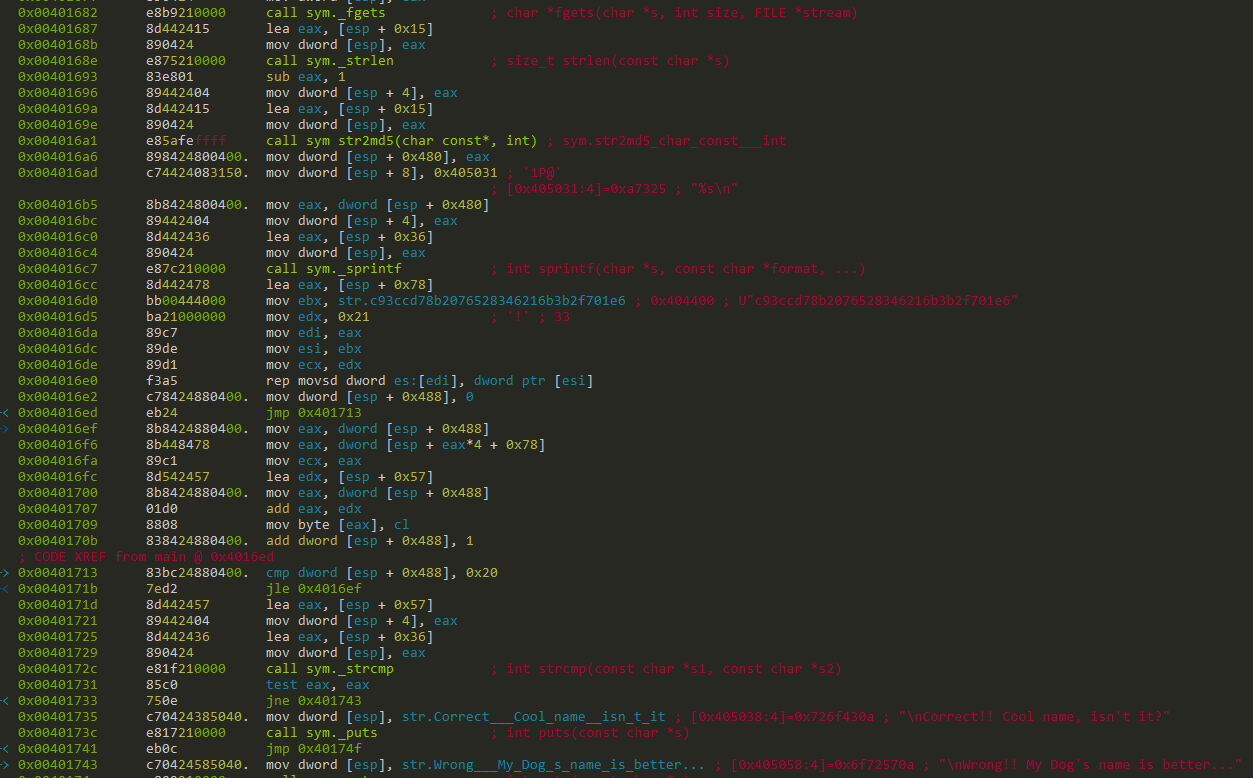
There is a function called named sym str2md5(char const*, int), looks like this takes an input string and hashes it with MD5.
Also there's a hardcoded string fitting into the MD5 format.
Let's take this string and try to dehash it, for dehashing we could either try an online service or fire up hashcat.
In this case I will first try my luck with https://crackstation.net before firing up hashcat.
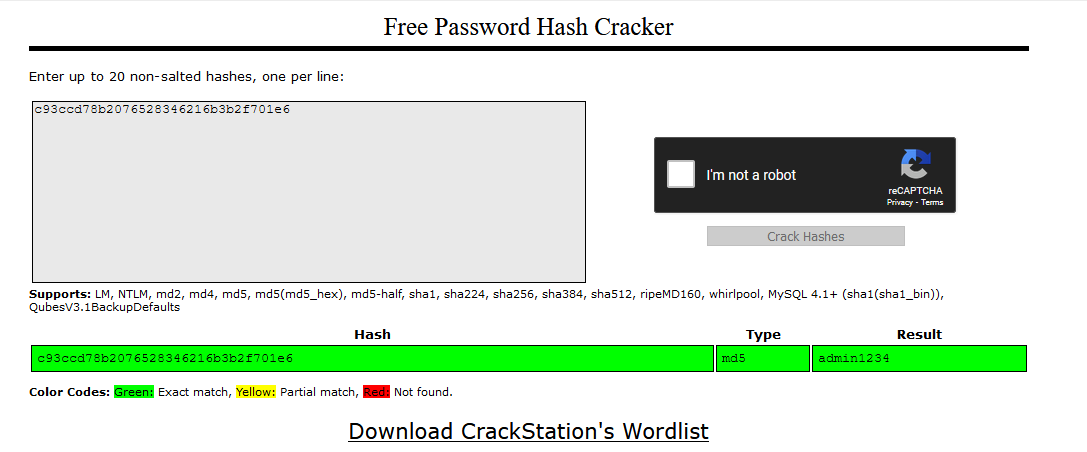
As assumed it's indeed a MD5 Hash and I even got a result: admin1234.
Let's start the application and test if this is actually his dog's name:
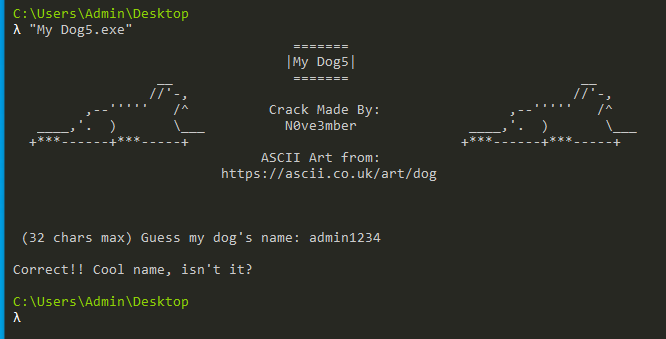
Success! We found his dog's name whether that's a good name or not is up to you...
Tags:
radare2, crackmes.one, reversing, crackme, reverse engineering, PE32