My Offensive Security Exploit Developer Review
Or: How I got the nickname "I Broke SMTP For Everyone" on the Offensive Security Discord server.
The Course Materials
They were tough... at least partially...
Before enrolling in WUMED I read through the amazing blog posts from Corelan in order to get into the world of exploit development before starting yet another OffSec journey. I already thought that Peter van Eeckhoutte from Corelan was pretty detailed in some topics but the course materials brought the level of going deeper to whole other dimensions.
Offensive Security did a great job covering basics like x86 shellcode writing, the Windows SEH, bypassing DEP and ASLR, and so on. Unfortunately, there was one thing I didn't like about the syllabus which is that stack canaries (aka. stack cookies) are not covered. In my opinion, they are pretty relevant and especially when talking about SEH-based Buffer Overflows you should also know about them.
But other than that, they were great and even though it took me way longer to read through the EXP-301 PDF than through the PEN-200 one, I really enjoyed the time studying it.
The Community
Is amazing.
I've met even more incredible people than during my OSCP journey and I am looking forward to meeting even more.
The biggest thank you goes to RootHomie aka. tr3sp4ss3r, who was crazy enough to invite someone he just knew from the OffSec discord to Sweden, so that we could both enjoy the SecurityFest conference and have some wonderful days and evenings after the conference before I got to Stockholm to get on my plane back.
A big thank you also goes to the crazy people like BONK (aka. windy bug) and ExAllocatePool2 (aka. Mr. SwimmingPool) that hang out with me in discord calls for hours and hours talking about exploit development and some pretty weird projects.
Another big thank you also goes to Tristram who is one of the kindest people I've met in my entire life. The best way to describe him is that if you lost all faith in humanity, he's the guy who can restore in less than 15 minutes.
And how can someone create such a big hype as S3L33 did??
And of course, there were many more like ShadowKhan, ApexPredator, Yizhigou, snowcrash, zammo, diss`, Affix, ... way too many to mention them all unfortunately.
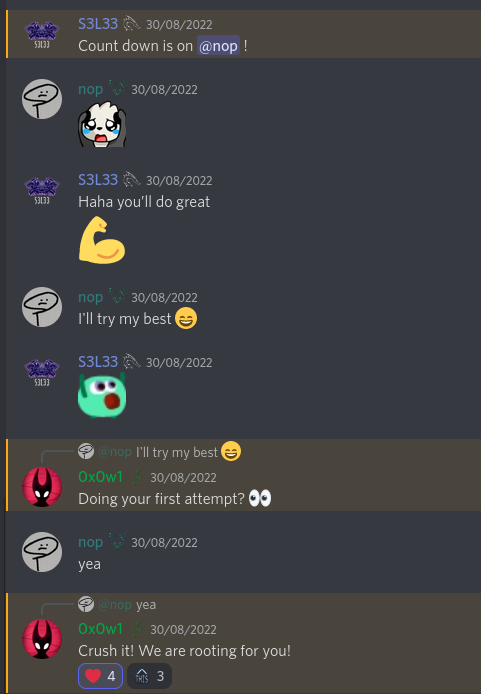
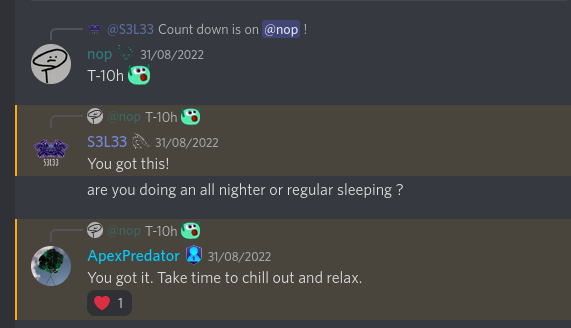
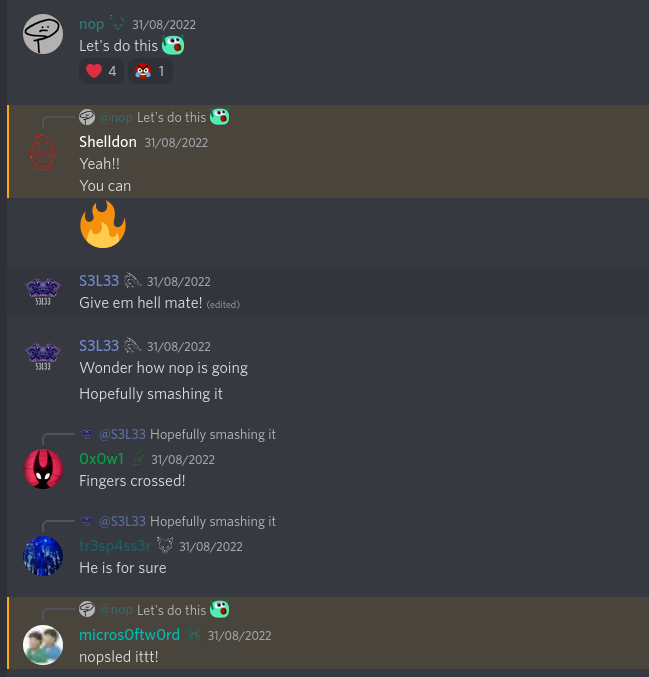
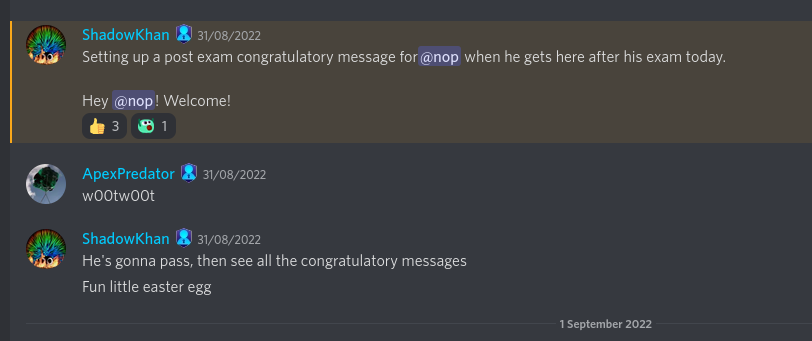
One thing I still cannot believe is the hype that was going on before and during my exam:
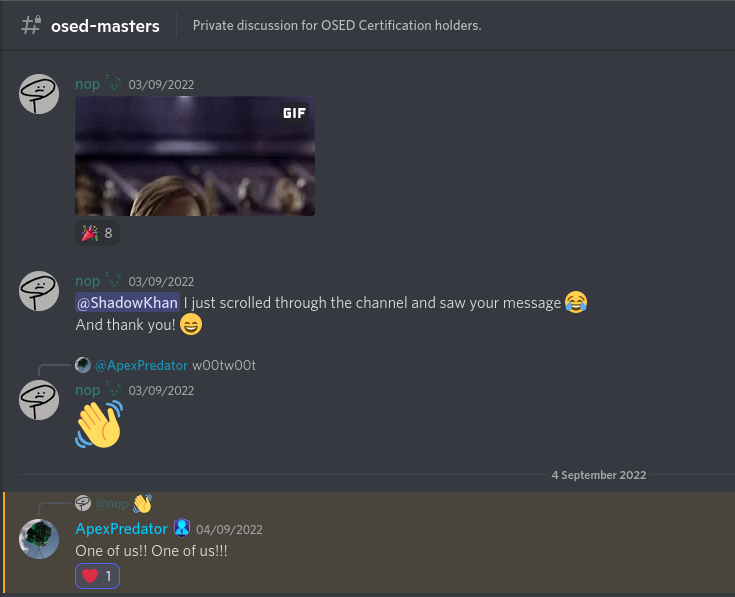
Lots of screenshots:
There are just too many kind direct messages from Tristram to put them all here.
The day / a few hours before my exam:
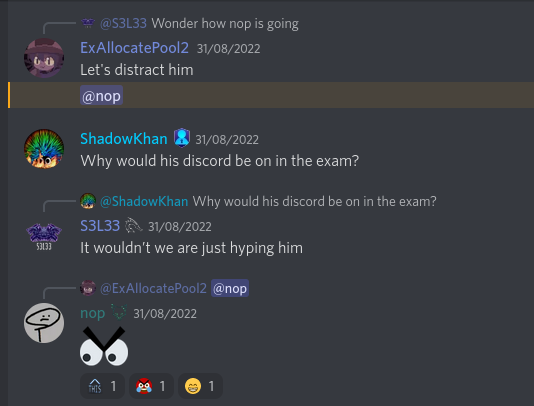

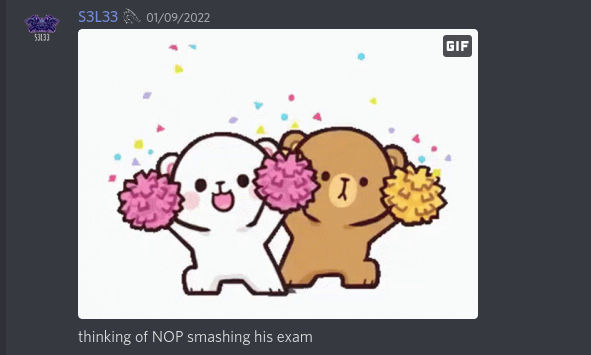
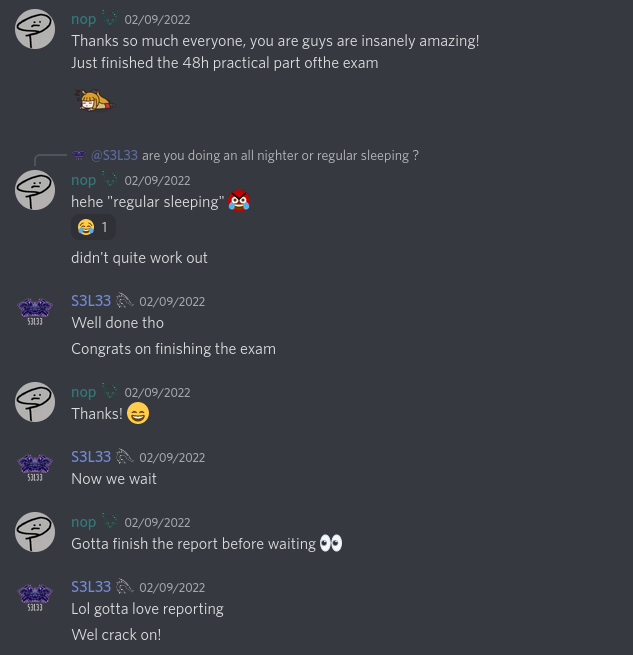
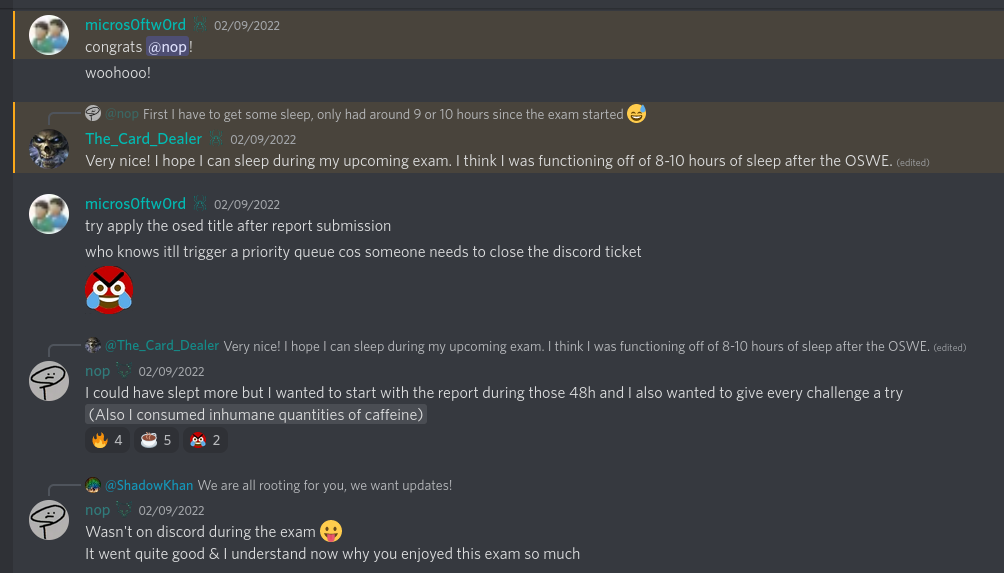
After the exam:

The Exam
nop did not stick to his plan.
nop also created calendar events that were supposed to remind him of eating breakfast, lunch, & dinner. nop neither stuck to this plan
I enjoyed this exam way more than the OSCP exam back in January this year. That's because while working on the exam, I constantly made progress which resulted in me rarely having the feeling of being stuck. Besides that, I just love working on those puzzles you will also encounter during the EXP-301 course e.g. ROP-chains.
Once again, my exam started at 11:00am and on the first day, I worked until around 01:00am of the next day, taking breaks every 60-90 minutes for 10-15 minutes. In addition to those regular short breaks, I also took ~2 longer breaks for around an hour.
During the 48h of the practical part I only slept around 9h - something I definitely would NOT recommend but it is what it is.
The Exam Grading
This time the grading was simply confusing.
I submitted my final exam report at around 02:45am and after sleeping for a few hours I woke up with a new color and role on the Offensive Security Discord server but I didn't receive the mail containing my results yet.
A few moments later Tristram messaged me that I passed but somehow didn't receive my mail yet. Sometime later the "Congratulations"-message showed up on the OffSec portal but still no mail...
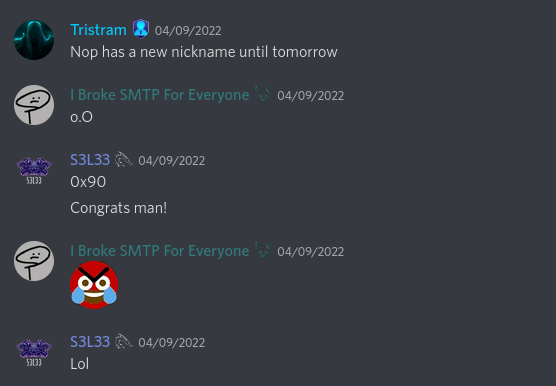
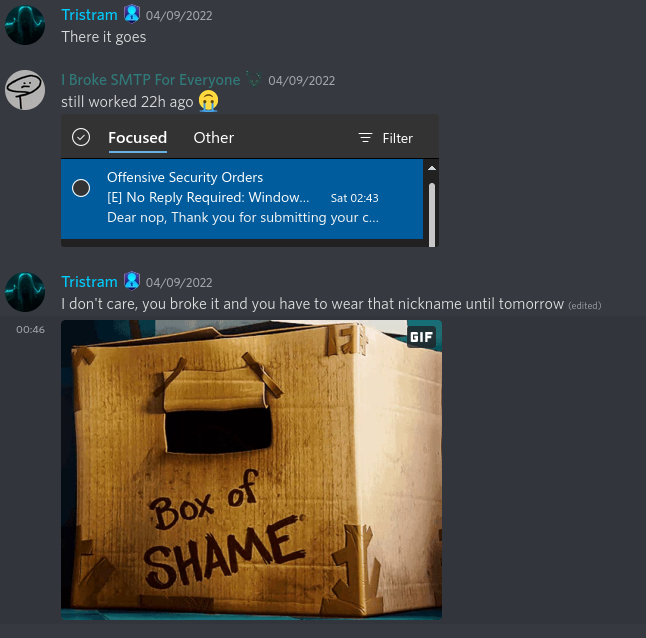
After discussing the matter on the OffSec discord server Tristram brought up the conspiracy theory that my handle being nop broke the SMTP server:
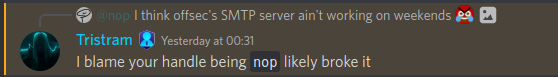
This also led to my new nickname:
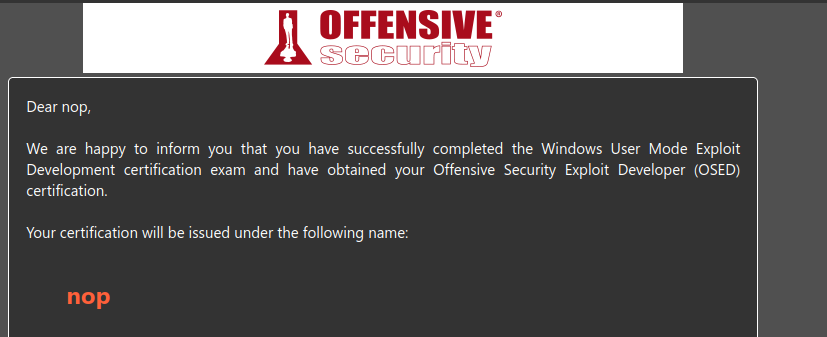
Eventually, just 25 hours (!) after submitting my report and having some confusing discussions I finally got the E-mail that I passed the OSED exam:
Conclusion
The EXP-301 (aka. WUMED) course is a great introductory into the world of windows userland exploitation and while it doesn't cover absolutely everything, it'll serve as a solid foundation to build upon.
I absolutely enjoyed studying the course materials, hanging out with other EXP-301 students (which definitely didn't end up in totally crazy conversations in the voice chat from 08:00pm to 07:00am), and eventually taking the exam.
If you are interested in windows exploit development and consider enrolling in EXP-301, don't let the others scare you; yes it's a tough course but it's far from being impossible and after getting comfortable with it and the community you'll love it.
Once again, thank you to all the amazing people I met and became friends with!
Even though I am taking a break from doing OffSec courses for ~1 year now in order to focus on my bachelor thesis, I am looking forward to taking the OSEP, OSWE and eventually the OSEE!
P.S.: Congratulations to biglittlealb who took the exam at the same day!
w00tw00t